My name is Cristian, I am a systems and security engineer.
Passionate about the world of computer science and cybersecurity.
I want to share with everything about the world of cybersecurity in a way easier to understand and bring it closer and closer.
Popular News
Highlights
Kerberos: Implementación, Análisis y Explotación
¿Qué es Kerberos? Kerberos es un protocolo de autenticación de red seguro…
Métodos de ataque: Command Injection
La inyección de comandos es un ciberataque que implica la ejecución de…
Kerberos Golden and Silver Ticket Attack
Hoy les traigo un tutorial muy sencillo y que mucha gente me…
Pentesting Active Directory con Responder
Muchas personas me están preguntando sobre métodos de prevención de ataque del…
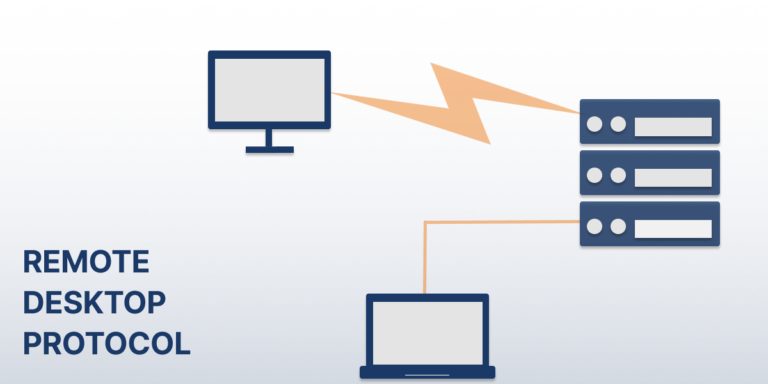
Remote Desktop Protocol (RDP)
El Protocolo de Escritorio Remoto (RDP) es un protocolo, o estándar técnico,…
Acceder a Windows 10 sin saber la contraseña
Seguro que a mas de uno le ha pasado que se ha…

Command Injection Vulnerability Discovered in Array AG Gateways: Urgent Action Required
Command Injection Vulnerability Discovered in Array AG Gateways: Urgent Action Required Overview of the Vulnerability JPCERT/CC recently issued a warning regarding the exploitation of a command injection vulnerability in Array Networks AG Series secure access gateways. This vulnerability has reportedly been active since August 2025, raising significant concerns about the security posture of its affected…
Critical Vulnerabilities in React Server Components Pose Serious Security Risks
Critical Vulnerabilities in React Server Components Pose Serious Security Risks Introduction to the Vulnerability A maximum-severity security flaw has been disclosed in React Server Components (RSC), which could potentially allow unauthenticated remote code execution. This critical vulnerability, tracked as CVE-2025-55182 and codenamed React2shell, has garnered attention within the developer community due to its severity, carrying…
Korean Police Crack Down on Illicit Trade of Hacked IP Camera Footage
Korean Police Crack Down on Illicit Trade of Hacked IP Camera Footage Overview of the Incident The recent arrests made by the Korean National Police highlight a disturbing trend in the exploitation of technology. Four suspects are accused of orchestrating a large-scale operation that compromised over 120,000 IP cameras throughout South Korea. The hacked footage,…
India Mandates Pre-Installation of Cybersecurity App to Combat Telecom Fraud
India Mandates Pre-Installation of Cybersecurity App to Combat Telecom Fraud Background and Context In a significant move aimed at enhancing cybersecurity within the telecommunications sector, India’s Ministry of Telecommunications has mandated that all mobile device manufacturers preload the Sanchar Saathi app on new devices within a 90-day window. This initiative responds to increasing concerns over…
Tomiris Adopts Public-Service Implants to Enhance C2 in Government Target Attacks
Tomiris Adopts Public-Service Implants to Enhance C2 in Government Target Attacks Background and Context The escalation of cyber warfare tactics has become increasingly evident in recent years, with groups like Tomiris adapting their methodologies to remain effective against evolving defenses. Founded around 2018, Tomiris has gained notoriety for its sophisticated attacks on both national governments…
Asahi Group Holdings Reports Cyberattack Affecting Nearly 1.9 Million Individuals
Asahi Group Holdings Reports Cyberattack Affecting Nearly 1.9 Million Individuals Background and Context Asahi Group Holdings, Japan’s leading beer producer and beverage conglomerate, has experienced a significant cyberattack that has impacted the personal data of approximately 1.9 million individuals. This incident, which was uncovered following an internal investigation of a September 2025 breach, underscores the…
Man Sentenced to Seven Years for In-Flight WiFi Data Theft
Man Sentenced to Seven Years for In-Flight WiFi Data Theft Background on WiFi Network Threats The rise of mobile technology has transformed the way individuals access information and communicate while traveling. However, it has also led to an increase in cybercrime, particularly in the realm of public WiFi networks. Hackers have developed various methods to…
OpenAI Confirms API Customer Data Breach Linked to Mixpanel Vendor Incident
OpenAI Confirms API Customer Data Breach Linked to Mixpanel Vendor Incident Background on the Breach OpenAI has recently informed a group of ChatGPT API customers that a data breach has occurred due to a vulnerability within its analytics service provider, Mixpanel. This incident highlights the increasing risks associated with third-party vendors, particularly in technology sectors…
ShadowV2 Botnet Exploits AWS Outage: A Deep Dive
ShadowV2 Botnet Exploits AWS Outage: A Deep Dive Background and Context The emergence of ShadowV2, a new Mirai-based botnet malware, marks a troubling development in the realm of cybersecurity, particularly for Internet of Things (IoT) devices. The recent attack exploited known vulnerabilities in widely used IoT hardware from manufacturers such as D-Link and TP-Link. This…
Nationwide Disruption of Emergency Alert Systems Following OnSolve CodeRED Cyberattack
Nationwide Disruption of Emergency Alert Systems Following OnSolve CodeRED Cyberattack Background and Context The recent cyberattack on OnSolve CodeRED has raised significant concerns about the resilience of emergency notification systems across the United States. OnSolve CodeRED, a risk management platform utilized by numerous state and local agencies, plays a critical role in disseminating urgent information…
StealC Infostealing Malware Distributed via Malicious Blender Files
StealC Infostealing Malware Distributed via Malicious Blender Files Introduction to the Threat Recent reports have identified a troubling campaign linked to Russian cybercriminals, utilizing targeted malicious Blender model files to distribute the StealC V2 information-stealing malware. As digital marketplaces for 3D models become increasingly popular among creative professionals, the infiltration of these platforms highlights significant…
Google Facilitates Seamless File Sharing Between Pixel Devices and iPhones
Google Facilitates Seamless File Sharing Between Pixel Devices and iPhones Introduction to the New Feature In a significant move aimed at enhancing cross-platform usability, Google has introduced interoperability between its Quick Share feature on Pixel devices and Apple’s AirDrop. This update allows users on either platform to easily share files with one another, marking an…
Security Flaw in WhatsApp API Exposes 3.5 Billion Accounts
Security Flaw in WhatsApp API Exposes 3.5 Billion Accounts Background and Context The recent discovery that researchers were able to compile a staggering list of 3.5 billion mobile phone numbers and associated personal information from WhatsApp has highlighted severe vulnerabilities in one of the world’s most popular messaging platforms. The flaw stems from a contact-discovery…
CISA Alerts on Active Exploitation of Oracle Identity Manager RCE Vulnerability
CISA Alerts on Active Exploitation of Oracle Identity Manager RCE Vulnerability Overview of the Vulnerability The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has issued a significant warning regarding an identified vulnerability in Oracle Identity Manager, designated as CVE-2025-61757. This flaw is classified as a remote code execution (RCE) vulnerability and is reportedly being actively…
Understanding Open-Source Intelligence: Safeguarding Your Digital Presence
Understanding Open-Source Intelligence: Safeguarding Your Digital Presence Introduction to Open-Source Intelligence In an era where digital interactions dominate personal and professional landscapes, understanding open-source intelligence (OSINT) has become crucial for individuals and organizations alike. OSINT refers to the process of gathering information from publicly accessible sources, enabling users to identify vulnerabilities in their digital presence…
Global Campaign Unleashes TamperedChef Malware via Deceptive Software Installers
Global Campaign Unleashes TamperedChef Malware via Deceptive Software Installers Background and Context The ongoing global malware campaign known as TamperedChef underscores the growing sophistication and reach of cybercriminal activities. This campaign capitalizes on the trust users place in popular software, employing bogus installers to introduce malicious payloads onto victim machines. As digital threats evolve, such…
Thunderbird 145 Introduces Native Microsoft Exchange Support
Thunderbird 145 Introduces Native Microsoft Exchange Support Introduction of Native Support for Microsoft Exchange On November 18, 2025, Thunderbird 145 was released, marking a significant advancement in the email client’s capabilities with the inclusion of full native support for Microsoft Exchange accounts via the Exchange Web Services (EWS) protocol. This development enables users to integrate…
Google Addresses Critical Chrome V8 Zero-Day Vulnerability with Urgent Security Update
Google Addresses Critical Chrome V8 Zero-Day Vulnerability with Urgent Security Update Introduction to the Vulnerability On November 18, 2025, Google announced essential security updates for its Chrome browser, targeting two vulnerabilities, including a critical zero-day flaw known as CVE-2025-13223. This particular vulnerability has a CVSS score of 8.8, indicating a significant security threat that attackers…
Google’s New Initiative to Identify Battery-Draining Android Apps
Google’s New Initiative to Identify Battery-Draining Android Apps Introduction In a significant move to enhance user experience and device efficiency, Google has announced that it will begin flagging Android applications in the Google Play Store that are associated with excessive background activity and battery drain. This initiative, set to commence in the coming months, aims…
Critical Vulnerability in Post SMTP Plugin Poses Risk to WordPress Sites
Critical Vulnerability in Post SMTP Plugin Poses Risk to WordPress Sites Background and Context The Post SMTP plugin has been widely adopted by WordPress users, offering reliable and easy-to-configure SMTP mail sending options. Installed on over 400,000 WordPress sites, its integration streamlines email communications for businesses and individual users alike. However, this popularity also makes…
Immediate Response Strategies Following a Cyberattack
Immediate Response Strategies Following a Cyberattack Background: The Growing Threat of Cyberattacks The evolution of technology has, paradoxically, given rise to increasingly sophisticated cyberattacks. According to a report by Cybersecurity Ventures, cybercrime is projected to inflict damages exceeding $10.5 trillion annually by 2025. This alarming statistic highlights the urgency for individuals and organizations to recognize…
Data Breach at University of Pennsylvania Exposes 1.2 Million Donor Records
Data Breach at University of Pennsylvania Exposes 1.2 Million Donor Records Background and Context On November 2, 2025, a hacker publicly claimed responsibility for a significant data breach at the University of Pennsylvania, revealing that 1.2 million donor records were compromised. This incident highlights ongoing vulnerabilities within educational institutions, particularly regarding how they manage and…
Google’s AI Search Integration: The Future of Advertising in a New Era
Google’s AI Search Integration: The Future of Advertising in a New Era Introduction to AI in Search Engines The integration of artificial intelligence (AI) in search engines marks a significant evolution in how information is retrieved online. As digital landscapes become increasingly competitive, companies like Google are continually adapting to user expectations and technological advancements.…
OpenAI Launches Aardvark: A Revolutionary GPT-5 Agent for Automated Code Flaw Detection and Mitigation
OpenAI Launches Aardvark: A Revolutionary GPT-5 Agent for Automated Code Flaw Detection and Mitigation Background and Context OpenAI, a leader in artificial intelligence research and development, has announced the launch of Aardvark, an innovative autonomous agent based on the GPT-5 architecture. This AI-driven tool is designed to perform the complex tasks of scanning, comprehending, and…
Enhancing macOS Security: Addressing Admin Errors to Mitigate Cyber Threats
Enhancing macOS Security: Addressing Admin Errors to Mitigate Cyber Threats Background & Context In recent years, operating systems have faced increasing scrutiny regarding their security measures. As cyber threats become more sophisticated, user error remains a significant vulnerability in the overall security landscape. This is particularly relevant for macOS, where a mix of robust design…
Malicious NPM Packages Compromise Sensitive Data Across Multiple Platforms
Malicious NPM Packages Compromise Sensitive Data Across Multiple Platforms Background and Context The discovery of ten malicious packages in the Node Package Manager (npm) registry highlights ongoing security vulnerabilities within software development environments. NPM, a vital component for JavaScript developers, facilitates the sharing and utilization of code libraries. However, its popularity also makes it a…
Critical Security Vulnerabilities Target Dassault Systèmes and XWiki
Critical Security Vulnerabilities Target Dassault Systèmes and XWiki Introduction to Recent Exploits Active exploitation of security flaws in Dassault Systèmes DELMIA Apriso and XWiki has come into focus following alerts from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and cybersecurity firm VulnCheck. These vulnerabilities pose significant risks to organizations using these platforms, highlighting a…
BiDi Swap: How Bidirectional Unicode Is Being Used to Make Fake URLs Appear Legitimate
BiDi Swap: How Bidirectional Unicode Is Being Used to Make Fake URLs Appear Legitimate What the BiDi Swap trick is and why it matters Security researchers at Varonis have documented a renewed phishing technique they call “BiDi Swap,” in which attackers abuse Unicode bidirectional (BiDi) control characters to make malicious URLs display as if they…
Qilin Ransomware Deploys Linux Payloads and BYOVD Tactics in Hybrid Attacks
Qilin Ransomware Deploys Linux Payloads and BYOVD Tactics in Hybrid Attacks Overview and key facts Security researchers have observed the Qilin ransomware operation — also tracked under the names Agenda, Gold Feather and Water Galura — using a hybrid attack approach that pairs a Linux-capable payload with a BYOVD (Bring Your Own Vulnerable Driver) exploitation…
CoPhish: Copilot Studio Agents Used to Steal OAuth Tokens via Trusted Microsoft Domains
CoPhish: Copilot Studio Agents Used to Steal OAuth Tokens via Trusted Microsoft Domains Overview Security researchers have identified a new phishing technique named “CoPhish” that leverages Microsoft Copilot Studio agents to deliver fraudulent OAuth consent prompts via legitimate Microsoft domains. The campaign uses the trust provided by Microsoft-owned infrastructure to present users with what appear…
194,000+ Domains Tied to Global Smishing Campaign, Unit 42 Warns
194,000+ Domains Tied to Global Smishing Campaign, Unit 42 Warns Summary of the Finding Palo Alto Networks Unit 42 has attributed more than 194,000 malicious domains to a large-scale, ongoing smishing campaign that has been active since January 1, 2024. The campaign, as reported by the security vendor, targets a wide range of services and…
Toys “R” Us Canada confirms customer records stolen and later leaked — what organizations and customers should do next
Toys “R” Us Canada confirms customer records stolen and later leaked — what organizations and customers should do next Summary of the incident Toys “R” Us Canada has notified customers that threat actors leaked customer records they had previously stolen from the retailer’s systems. The company’s breach notification, shared with affected customers, indicates an incident…
Critical Adobe Commerce/Magento Vulnerability Exploited in Over 250 Attack Attempts
Critical Adobe Commerce/Magento Vulnerability Exploited in Over 250 Attack Attempts What happened Security researchers at e-commerce protection firm Sansec reported that threat actors have begun actively exploiting a recently disclosed vulnerability affecting Adobe Commerce and Magento Open Source. The flaw is tracked as CVE-2025-54236 and carries a CVSS score of 9.1. Sansec recorded more than…
TP-Link Fixes Four Omada Gateway Vulnerabilities, Two Allow Arbitrary Code Execution
TP-Link Fixes Four Omada Gateway Vulnerabilities, Two Allow Arbitrary Code Execution What the update fixes TP-Link has released security updates addressing four vulnerabilities in its Omada gateway devices, including two critical flaws that can lead to arbitrary code execution. One of the flaws has been publicly identified as CVE-2025-6541 (CVSS 8.6), an operating system command…
DNS0.EU Public DNS Service Shuts Down Citing Sustainability Constraints
DNS0.EU Public DNS Service Shuts Down Citing Sustainability Constraints What happened DNS0.EU, a non-profit public DNS resolver that served primarily European users, announced an immediate shutdown, attributing the decision to time and resource constraints. The project’s operators said they were unable to continue running the service under current conditions and ceased operations with immediate effect.…
TikTok “ClickFix” Videos Deliver Info‑Stealers via Fake Activation Guides
TikTok “ClickFix” Videos Deliver Info‑Stealers via Fake Activation Guides Summary of the campaign Security researchers are tracking a surge of so‑called “ClickFix” attacks that use short TikTok videos posing as free activation or “fix” guides for popular software — including Windows, Spotify and Netflix — to trick users into downloading information‑stealing malware. The videos present…
OpenAI: GPT-6 Will Not Ship in 2025 — Implications for Developers, Enterprises, and Policymakers
OpenAI: GPT-6 Will Not Ship in 2025 — Implications for Developers, Enterprises, and Policymakers What OpenAI confirmed OpenAI has confirmed that GPT-6 will not be shipped in 2025. The company’s statement clarified that while a major labelled release is not planned for this calendar year, this does not preclude the release of other models, updates,…
ConnectWise patches Automate flaw that enabled AiTM-style tampering of updates
ConnectWise patches Automate flaw that enabled AiTM-style tampering of updates Summary of the update ConnectWise released a security update for its Automate remote monitoring and management (RMM) product to fix multiple vulnerabilities, including one the company classified as critical. According to reporting, the most serious issue could allow adversaries to intercept and modify sensitive communications…
Windows 11 October Update Breaks Localhost HTTP/2 (127.0.0.1) Connections
Windows 11 October Update Breaks Localhost HTTP/2 (127.0.0.1) Connections Summary of the issue Reports surfaced after Microsoft’s October 2025 Windows 11 updates that applications attempting to connect to the loopback address (127.0.0.1) over HTTP/2 are failing to establish or maintain connections. Affected workflows include local development servers, desktop applications that talk to bundled local services,…
YouTube outage triggers global playback errors on web and mobile
YouTube outage triggers global playback errors on web and mobile Incident overview Users around the world are experiencing playback errors on YouTube’s website and mobile applications, indicating a global outage affecting video streaming functionality. Reports describe failures when attempting to play videos across platforms, and users on social media and monitoring sites are flagging widespread…
Using NDR to Detect Dark Web‑Sourced Threats on Your Network
Using NDR to Detect Dark Web‑Sourced Threats on Your Network Why this matters: background and context Activity originating from dark web marketplaces and criminal forums increasingly fuels enterprise breaches. Threat actors buy and sell stolen credentials, remote access tools, malware, and exploit code on those platforms, lowering the barrier to entry for malicious campaigns. When…
Synced Passkeys: Cloud Convenience That Reintroduces Account Recovery Risk
Synced Passkeys: Cloud Convenience That Reintroduces Account Recovery Risk Background: what passkeys are and why synced ones matter Passkeys (FIDO/WebAuthn credentials) are cryptographic credentials bound to a user’s device or authenticator that are designed to replace passwords and resist phishing. They eliminate shared secrets: instead of typing a password, a relying party verifies a public…
WhatsApp Worm to Oracle Zero‑Day: This Week’s Cross‑Platform Attack Chains
WhatsApp Worm to Oracle Zero‑Day: This Week’s Cross‑Platform Attack Chains Overview: quiet starts, loud consequences Every week the cyber world reminds us that silence doesn’t mean safety. Attacks frequently begin with a single unpatched flaw, an overlooked credential, or a backup left unencrypted. By the time alarms go off, adversaries have already chained multiple weaknesses,…
SonicWall SSL VPN Devices Reportedly Compromised at Scale; Valid Credentials Suspected
SonicWall SSL VPN Devices Reportedly Compromised at Scale; Valid Credentials Suspected Summary of the incident Cybersecurity firm Huntress on Friday warned of a “widespread compromise” of SonicWall SSL VPN devices that attackers are using to access multiple customer environments. According to the alert, threat actors are authenticating into multiple accounts rapidly across compromised devices. The…
ClayRat Android Spyware Distributes via Fake WhatsApp, TikTok and Other App Lures in Russia
ClayRat Android Spyware Distributes via Fake WhatsApp, TikTok and Other App Lures in Russia Overview of the campaign Security researchers have identified a rapidly evolving Android spyware campaign dubbed “ClayRat” that has targeted users in Russia. According to reporting, operators behind the campaign used a mix of Telegram channels and lookalike phishing websites to entice…
ShinyHunters Escalates Extortion Against Red Hat After Customer Engagement Reports Leak
ShinyHunters Escalates Extortion Against Red Hat After Customer Engagement Reports Leak What happened Enterprise software vendor Red Hat is facing an extortion campaign after the ShinyHunters criminal group posted samples of stolen customer engagement reports (CERs) on its data leak site. The leaked artifacts were described as samples from an alleged data theft and were…
Microsoft investigates Copilot failures when multiple Office apps run simultaneously
Microsoft investigates Copilot failures when multiple Office apps run simultaneously Summary of the incident Microsoft is investigating a bug that causes Copilot issues when multiple Office apps are running simultaneously on the same system. Microsoft is investigating a bug that causes Copilot issues when multiple Office apps are running simultaneously on the same system. Reports…
Zimbra Zero-Day Abused via iCalendar (.ICS) Files — What Administrators Need to Know
Zimbra Zero-Day Abused via iCalendar (.ICS) Files — What Administrators Need to Know Summary of the incident Researchers monitoring for unusually large .ICS calendar attachments discovered that a flaw in Zimbra Collaboration Suite (ZCS) was actively exploited as a zero-day earlier this year. The attackers used iCalendar files to trigger the vulnerability, enabling compromise of…
Zimbra Zero‑Day Abused via Malicious iCalendar (.ICS) Attachments
Zimbra Zero‑Day Abused via Malicious iCalendar (.ICS) Attachments Summary of the discovery Researchers monitoring for larger .ICS calendar attachments found that a flaw in Zimbra Collaboration Suite (ZCS) was used in zero-day attacks at the beginning of the year. That finding indicates attackers leveraged the iCalendar format — commonly used for meeting invites and calendar…
Leaked iPad Pro M5 Benchmark Suggests Near-Desktop Performance
Leaked iPad Pro M5 Benchmark Suggests Near-Desktop Performance What the leak shows A newly leaked benchmark result, attributed to an iPad Pro running what is being described as Apple’s alleged M5 chip, indicates a substantial jump in raw performance — enough that the device approaches the speed of many desktop-class CPUs. The dataset appears limited…
OpenAI updates GPT-5 to close emotional-support gap with GPT-4o
OpenAI updates GPT-5 to close emotional-support gap with GPT-4o At a glance According to reporting from BleepingComputer, OpenAI has rolled out an update intended to improve GPT-5’s ability to provide emotional support. The outlet observed that GPT-5 had previously underperformed relative to GPT-4o on supportive, empathetic interactions, and that the change released today aims to…
Detour Dog Linked to DNS-Enabled Distribution of Strela Stealer via StarFish Backdoor
Detour Dog Linked to DNS-Enabled Distribution of Strela Stealer via StarFish Backdoor Summary of findings Security researchers at DNS threat intelligence firm Infoblox have attributed a series of information-stealer campaigns to a threat actor tracked as “Detour Dog.” According to Infoblox, Detour Dog maintained operational control over domains that hosted the first-stage component of the…
Signal introduces SPQR to harden messaging against future quantum attacks
Signal introduces SPQR to harden messaging against future quantum attacks What Signal announced Signal has unveiled a new cryptographic component called Sparse Post-Quantum Ratchet (SPQR). The company presents SPQR as an addition to its existing end-to-end encryption design intended to provide stronger resilience against the kinds of attacks that could be enabled by large-scale quantum…
Confucius Campaign in Pakistan Deploys WooperStealer and Anondoor in Spear‑Phishing Attacks
Confucius Campaign in Pakistan Deploys WooperStealer and Anondoor in Spear‑Phishing Attacks Campaign summary Security researchers have attributed a recent phishing campaign against targets in Pakistan to the threat actor known as Confucius, which used the information‑stealer WooperStealer alongside a secondary payload referred to as Anondoor. According to reporting, the campaign employed spear‑phishing and malicious documents…
DrayTek Issues Advisory: Remote, Unauthenticated RCE Vulnerability in Vigor Routers
DrayTek Issues Advisory: Remote, Unauthenticated RCE Vulnerability in Vigor Routers What DrayTek reported Networking vendor DrayTek has published an advisory warning of a security vulnerability that affects several Vigor router models. According to the advisory, the flaw could allow remote, unauthenticated actors to execute arbitrary code on impacted devices. DrayTek’s notice alerts administrators and operators…
Ransomware at Motility Software Exposes Data of 766,000 Dealership Customers
Ransomware at Motility Software Exposes Data of 766,000 Dealership Customers Summary of the incident A ransomware attack targeting Motility Software Solutions, a provider of dealer management software (DMS), has exposed sensitive information belonging to approximately 766,000 customers. The incident underscores the systemic risk created when technology vendors that serve many organizations are compromised — a…
F‑Droid at risk as Google enforces identity verification for all Android developers
F‑Droid at risk as Google enforces identity verification for all Android developers Summary of the change and immediate concern F‑Droid, the volunteer‑run catalog and installer for free and open‑source Android applications, has warned that Google’s new requirement for all Android developers to verify their identity could threaten the project’s continued operation. The change obligates developer…
“Battering RAM” Hardware Interposer Can Bypass Intel and AMD Cloud Defenses, Researchers Show
“Battering RAM” Hardware Interposer Can Bypass Intel and AMD Cloud Defenses, Researchers Show Summary of the disclosure Researchers from KU Leuven and the University of Birmingham have demonstrated a practical hardware attack they call “Battering RAM,” using a low-cost interposer that sits in the DRAM channel and can bypass recent security protections on Intel and…
Phantom Taurus: China‑Linked Group Deploys Stealth Malware Against Governments and Telecoms
Phantom Taurus: China‑Linked Group Deploys Stealth Malware Against Governments and Telecoms Overview Security researchers at Palo Alto Networks Unit 42 have identified a previously undocumented, China‑aligned nation‑state actor they call “Phantom Taurus.” According to Unit 42, Phantom Taurus has operated for roughly two and a half years, targeting government and telecommunications organizations across Africa, the…
EvilAI Campaign: Malware Masquerading as AI Tools to Seed Global Intrusions
EvilAI Campaign: Malware Masquerading as AI Tools to Seed Global Intrusions Summary of the discovery Security researchers have identified a campaign in which threat actors use seemingly legitimate artificial intelligence (AI) and productivity tools as the delivery mechanism for malware. According to Trend Micro, attackers are deploying these AI-enhanced or productivity applications to slip malicious…
EvilAI Campaign: Malware Delivered Through Trojanized AI and Productivity Tools
EvilAI Campaign: Malware Delivered Through Trojanized AI and Productivity Tools Summary of the discovery Security researchers at Trend Micro have identified a campaign in which threat actors distribute malware by posing as legitimate artificial intelligence (AI) tools and productivity software. The operators deliver trojanized installers and seemingly benign utilities that, once executed, establish footholds for…
Akira Ransomware Bypassing OTP-Protected SonicWall SSL VPN Accounts — What Practitioners Need to Know
Akira Ransomware Bypassing OTP-Protected SonicWall SSL VPN Accounts — What Practitioners Need to Know Overview of the incident Security researchers tracking ongoing attacks by the Akira ransomware group report the actors have been successfully authenticating to SonicWall SSL VPN accounts even when one-time passcode (OTP) multi-factor authentication (MFA) is enabled. Initial analysis suggests the likely…
EU Opens Antitrust Probe into SAP’s Aftermarket Support for On-Premise ERP
EU Opens Antitrust Probe into SAP’s Aftermarket Support for On-Premise ERP What the Commission is investigating On 28 September 2025 the European Commission announced a probe into whether SAP has engaged in anti-competitive practices in the aftermarket services it provides for its on‑premise enterprise resource planning (ERP) software. The investigation focuses on the market for…
Malvertising and SEO Poisoning Deliver Fake Microsoft Teams Installers that Install Oyster Backdoor
Malvertising and SEO Poisoning Deliver Fake Microsoft Teams Installers that Install Oyster Backdoor Summary of the campaign Security researchers have observed attackers using search engine optimization (SEO) poisoning and paid search advertisements to surface malicious pages that present fake Microsoft Teams installers to Windows users. When downloaded and executed, these installers deploy the Oyster backdoor,…
China-linked PlugX Variant and Bookworm Campaign Target Asian Telecoms and ASEAN Networks
China-linked PlugX Variant and Bookworm Campaign Target Asian Telecoms and ASEAN Networks Summary of the campaign Security reporting highlights an ongoing campaign that is distributing a new variant of the PlugX backdoor (also known as Korplug or SOGU) while targeting telecommunications and manufacturing organizations across Central and South Asia, with impacts reported in ASEAN networks.…
Microsoft Tests AI Auto-Categorization for Photos on Windows 11
Microsoft Tests AI Auto-Categorization for Photos on Windows 11 Overview Microsoft has begun testing a new AI-powered capability in the Microsoft Photos app that automatically organizes photos on Windows 11 devices. The feature, currently in testing, is intended to categorize images to make search and browsing faster and more intuitive. Microsoft’s announcement signals another major…
Trump Signs Order Approving US Investors to Restructure TikTok Operations over National Security Concerns
Trump Signs Order Approving US Investors to Restructure TikTok Operations over National Security Concerns Overview of the executive order U.S. President Donald Trump has signed an executive order approving a plan to restructure TikTok operations in the country to address national security concerns. The measure authorizes a change in the ownership and operational control of…
Critical Cisco ASA/FTD VPN Zero-Day Exploited in the Wild; CISA Issues Emergency Mitigation
Critical Cisco ASA/FTD VPN Zero-Day Exploited in the Wild; CISA Issues Emergency Mitigation Summary of the incident Cisco has alerted customers to two security flaws affecting the VPN web server component of Cisco Secure Firewall Adaptive Security Appliance (ASA) Software and Cisco Secure Firewall Threat Defense (FTD) Software, noting active exploitation in the wild. One…
Salesforce Patches Critical “ForcedLeak” Flaw in Agentforce That Could Expose CRM Data via Indirect Prompt Injection
Salesforce Patches Critical “ForcedLeak” Flaw in Agentforce That Could Expose CRM Data via Indirect Prompt Injection What happened Cybersecurity researchers at Noma Security disclosed a critical vulnerability in Salesforce Agentforce — the vendor’s platform for building AI-driven agents — that could allow attackers to exfiltrate sensitive information from a connected Salesforce CRM instance by leveraging…
Recorded Future Names Chinese State-Sponsored Cluster “RedNovember” Using Pantegana and Cobalt Strike
Recorded Future Names Chinese State-Sponsored Cluster “RedNovember” Using Pantegana and Cobalt Strike Background and context Security firm Recorded Future, which had been tracking an activity cluster under the tracking name TAG-100, has reclassified the cluster as a Chinese state-sponsored threat actor and given it the name RedNovember. The activity has been observed targeting government and…
Cisco issues urgent patch for actively exploited IOS and IOS XE zero-day
Cisco issues urgent patch for actively exploited IOS and IOS XE zero-day Summary of the advisory Cisco has released security updates to address a high-severity zero-day vulnerability in Cisco IOS and IOS XE Software that is being actively exploited in the wild. Cisco has released security updates to address a high-severity zero-day vulnerability in Cisco…
One Weak Password Ended a 158-Year-Old Logistics Firm
One Weak Password Ended a 158-Year-Old Logistics Firm The incident in brief KNP Logistics Group, a company with roots stretching back 158 years and formerly known as Knights of Old, has ceased operations after an incident tied to a single compromised or weak password. The business had built a substantial transport operation over its lifetime,…
BadIIS SEO-Poisoning Campaign Redirects Traffic and Installs Web Shells in Vietnam and Southeast Asia
BadIIS SEO-Poisoning Campaign Redirects Traffic and Installs Web Shells in Vietnam and Southeast Asia Summary of the discovery Cybersecurity researchers have identified an SEO poisoning campaign that uses malicious search-result manipulation to infect or redirect visitors and then deploy a malware family dubbed “BadIIS.” The activity, tracked by Palo Alto Networks Unit 42 as CL-UNK-1037…
Microsoft begins Windows 11 beta rollout of AI-powered Gaming Copilot
Microsoft begins Windows 11 beta rollout of AI-powered Gaming Copilot Overview of the rollout Microsoft has started a staged beta rollout of Gaming Copilot to Windows 11 PCs. The company is making the beta available to users aged 18 or older, but the rollout explicitly excludes devices located in mainland China. Microsoft has begun rolling…
Microsoft Begins Beta Rollout of Gaming Copilot for Windows 11 PCs
Microsoft Begins Beta Rollout of Gaming Copilot for Windows 11 PCs Overview of the rollout Microsoft has started a beta rollout of Gaming Copilot to Windows 11 systems. The initial deployment is limited to users who are 18 years or older and excludes availability in mainland China. Microsoft’s announcement positions the release as an expansion…
UNC1549 Campaign Compromises 34 Devices at 11 European Telecom Firms Using LinkedIn Job Lures and MINIBIKE Malware
UNC1549 Campaign Compromises 34 Devices at 11 European Telecom Firms Using LinkedIn Job Lures and MINIBIKE Malware Summary Security researchers have attributed a recent espionage campaign targeting European telecommunications companies to the cluster known as UNC1549. According to reporting by thehackernews.com and tracking by Swiss cybersecurity firm PRODAFT, the actor (tracked by PRODAFT as “Subtle…
Automating Alert Triage with AI Agents and Confluence SOPs Using Tines
Automating Alert Triage with AI Agents and Confluence SOPs Using Tines Summary of the workflow The workflow highlighted by Tines automates security alert triage by using AI-driven agents to identify the correct Standard Operating Procedures (SOPs) documented in Confluence, and then executing the appropriate response steps through the platform. The underlying Tines library — maintained…
OpenAI adds user control over GPT‑5 “thinking” depth for Plus and Pro subscribers
OpenAI adds user control over GPT‑5 “thinking” depth for Plus and Pro subscribers What OpenAI announced OpenAI has begun rolling out a new toggle that lets users select how “hard” the GPT‑5‑thinking model should work on a given prompt. The feature is being made available to ChatGPT Plus and Pro subscribers, enabling users to adjust…
SonicWall Urges Password Resets After Cloud Backup Files Accessed in MySonicWall Breach
SonicWall Urges Password Resets After Cloud Backup Files Accessed in MySonicWall Breach Incident summary SonicWall has notified customers that it detected suspicious activity targeting its cloud backup service for firewalls and that unknown threat actors accessed firewall configuration backup files stored in the cloud for less than 5% of MySonicWall accounts. The vendor has urged…
CountLoader: New Multi‑Version Loader Fuels Russian Ransomware Operations
CountLoader: New Multi‑Version Loader Fuels Russian Ransomware Operations Overview of the discovery Security researchers have identified a new malware loader, tracked as “CountLoader,” that is being used by Russian-affiliated threat actors to deliver post‑exploitation tools and remote access malware. According to published reporting, CountLoader has been observed distributing Cobalt Strike, AdaptixC2, and a remote access…
Attack methods: Buffer Overflow Attack
What is buffer overflow? Buffer overflow is an anomaly that occurs when software writing data to a buffer overflows its capacity, causing adjacent memory locations to be overwritten. In other words, too much information is passed to a container that does not have enough space, and that information ends up replacing the data in adjacent…
TA558 Deploys Venom RAT Using AI-Generated Scripts Against Hotels in Brazil and Spanish-Speaking Markets
TA558 Deploys Venom RAT Using AI-Generated Scripts Against Hotels in Brazil and Spanish-Speaking Markets Overview Russian security vendor Kaspersky has attributed a fresh campaign to the threat actor tracked as TA558 that delivered multiple remote access trojans (RATs), including Venom RAT, to breach hotels in Brazil and other Spanish-speaking markets. Kaspersky observed the activity in…
Microsoft and Cloudflare Disrupt RaccoonO365 Phishing-as-a-Service That Stole Thousands of Microsoft 365 Credentials
Microsoft and Cloudflare Disrupt RaccoonO365 Phishing-as-a-Service That Stole Thousands of Microsoft 365 Credentials Incident summary Microsoft and Cloudflare have jointly disrupted a large-scale Phishing-as-a-Service (PhaaS) operation known as RaccoonO365. According to reporting, the service enabled cybercriminals to run tailored Microsoft 365 credential-harvesting campaigns and helped steal thousands of Microsoft 365 credentials. The action targeted the…
BreachForums Admin Conor Fitzpatrick Resentenced to Three Years Following Appeals Court Reversal
BreachForums Admin Conor Fitzpatrick Resentenced to Three Years Following Appeals Court Reversal Summary of the ruling On September 16, 2025, Conor Brian Fitzpatrick, a 22-year-old identified as the administrator of the BreachForums hacking forum, was resentenced to three years in prison after a federal appeals court overturned his prior sentence of time served and 20…
Chaos Mesh GraphQL Flaws Could Enable RCE and Full Kubernetes Cluster Takeover
Chaos Mesh GraphQL Flaws Could Enable RCE and Full Kubernetes Cluster Takeover Disclosure summary Cybersecurity researchers have disclosed multiple critical vulnerabilities in Chaos Mesh — an open‑source chaos engineering platform for Kubernetes — that, if exploited, could allow remote code execution (RCE) and full takeover of Kubernetes clusters. The published advisory indicates attackers require only…
OpenAI Rolls Out GPT-5 Codex Across Codex Terminal, IDE Extension, and Web
OpenAI Rolls Out GPT-5 Codex Across Codex Terminal, IDE Extension, and Web What OpenAI announced OpenAI is rolling out the GPT-5 Codex model to all Codex instances, including Terminal, the IDE extension, and Codex Web (codex.chatgpt.com). The move places OpenAI’s latest code-specialized model directly into the workflows used by developers and teams, and positions it…
Mustang Panda Uses SnakeDisk USB Worm to Deliver Yokai Backdoor to Thailand-Based Targets
Mustang Panda Uses SnakeDisk USB Worm to Deliver Yokai Backdoor to Thailand-Based Targets Summary of the discovery IBM X-Force researchers Golo Mühr and Joshua Chung reported that the China-aligned threat actor known as Mustang Panda has deployed an updated TONESHELL backdoor alongside a previously undocumented USB worm called SnakeDisk. According to the analysis, the worm…
Browser-Based Attacks: What Security Teams Need to Prepare For Now
Browser-Based Attacks: What Security Teams Need to Prepare For Now What is a browser-based attack — and why it matters Attacks that target users in their web browsers have seen an unprecedented rise in recent years. A browser-based attack leverages the browser — and the rich, interactive content it renders — as the primary attack…
FBI Alert: UNC6040 and UNC6395 Target Salesforce Orgs for Data Theft and Extortion
FBI Alert: UNC6040 and UNC6395 Target Salesforce Orgs for Data Theft and Extortion What the FBI alert says The FBI has issued a FLASH alert warning that two threat clusters, tracked as UNC6040 and UNC6395, are compromising organizations’ Salesforce environments to steal data and extort victims. The FBI has issued a FLASH alert warning that…
FBI: UNC6040 and UNC6395 Target Salesforce Instances to Steal Data and Extort Victims
FBI: UNC6040 and UNC6395 Target Salesforce Instances to Steal Data and Extort Victims Summary of the FBI FLASH alert The FBI has issued a FLASH warning that two threat clusters, tracked as UNC6040 and UNC6395, are compromising organizations’ Salesforce environments to steal data and extort victims. The advisory raises immediate concern for enterprises that rely…
HybridPetya Ransomware Can Circumvent UEFI Secure Boot to Modify EFI System Partition
HybridPetya Ransomware Can Circumvent UEFI Secure Boot to Modify EFI System Partition Overview A recently reported ransomware strain known as HybridPetya is capable of bypassing the UEFI Secure Boot mechanism to place a malicious application on the EFI System Partition (ESP). The ability to write to the ESP and persist at or before the operating…
Three Immediate Priorities During a Cyberattack: Clarity, Control, Lifeline
Three Immediate Priorities During a Cyberattack: Clarity, Control, Lifeline Overview When a cyberattack begins, response speed and the sequence of actions determine whether an organization contains damage or faces prolonged disruption. A concise framework highlighted by Acronis TRU — clarity, control, and a lifeline — captures the immediate priorities MSPs and IT teams need to…
Microsoft resolves streaming lag and stutter introduced by August 2025 Windows updates
Microsoft resolves streaming lag and stutter introduced by August 2025 Windows updates Summary of the incident Microsoft has resolved severe lag and stuttering issues that affected streaming software on Windows 10 and Windows 11 systems following the installation of the August 2025 security updates. Users reported degraded playback and interrupted live streams after the update;…
US Charges Alleged Administrator of LockerGoga, MegaCortex, and Nefilim Ransomware
US Charges Alleged Administrator of LockerGoga, MegaCortex, and Nefilim Ransomware Summary of the DOJ Action The U.S. Department of Justice has charged Ukrainian national Volodymyr Viktorovich Tymoshchuk for his alleged role as the administrator of three major ransomware operations: LockerGoga, MegaCortex, and Nefilim. This charging announcement aligns with an ongoing law-enforcement campaign to identify, charge,…
How CISOs Win Budget Approval: Framing Security as Business Risk Management
How CISOs Win Budget Approval: Framing Security as Business Risk Management Why the budget fight matters now It’s budget season. Once again, security is being questioned, scrutinized, or deprioritized. For many organizations the security function remains a cost center competing with product development, sales initiatives, and operational efficiency projects. Yet the consequences of underfunding security…
Salesloft GitHub Account Compromise Triggered Drift Supply‑Chain Breach, Mandiant Says
Salesloft GitHub Account Compromise Triggered Drift Supply‑Chain Breach, Mandiant Says Summary of the incident Salesloft has disclosed that the chain of events behind a data breach tied to its Drift application began with the compromise of a Salesloft GitHub account. Google-owned Mandiant, which investigated the incident, reported that the threat actor tracked as UNC6395 accessed…
Drift Breach and a Week of Active Zero‑Days: What Security Teams Must Do Now
Drift Breach and a Week of Active Zero‑Days: What Security Teams Must Do Now Overview — this week’s headlines Cybersecurity coverage this week was dominated by two interlocking themes: a high‑visibility breach involving the conversational marketing vendor Drift, and a wave of active zero‑day exploits prompting urgent patch warnings. Reporting and vendor advisories emphasized the…
SVG-based phishing campaign impersonates Colombian judiciary to deliver malware
SVG-based phishing campaign impersonates Colombian judiciary to deliver malware The campaign: what VirusTotal uncovered Security researchers at VirusTotal have identified a phishing campaign that hides malicious content inside Scalable Vector Graphics (SVG) files. The SVGs are designed to render convincing portal pages that impersonate Colombia’s judicial system, and they act as delivery mechanisms for malware.…
Microsoft Enforces MFA for Azure Portal Sign‑Ins Across All Tenants
Microsoft Enforces MFA for Azure Portal Sign‑Ins Across All Tenants What Microsoft changed Microsoft says it has been enforcing multifactor authentication (MFA) for Azure Portal sign‑ins across all tenants since March 2025. Microsoft has been enforcing multifactor authentication for Azure Portal sign‑ins across all tenants since March 2025. The change applies to interactive access to…
Critical SAP S/4HANA Code Injection Vulnerability Actively Exploited
Critical SAP S/4HANA Code Injection Vulnerability Actively Exploited Overview: what has been observed Security researchers are reporting active exploitation of a critical code injection vulnerability in SAP S/4HANA, used by attackers to compromise internet-exposed systems. The flaw allows an attacker to inject and execute code on vulnerable S/4HANA instances, giving them a pathway to escalate…
Cloudflare Says It Mitigated a Record 11.5 Tbps Volumetric DDoS Attack
Cloudflare Says It Mitigated a Record 11.5 Tbps Volumetric DDoS Attack What Cloudflare reported Cloudflare announced that its network automatically mitigated a volumetric distributed denial-of-service (DDoS) attack that peaked at 11.5 terabits per second (Tbps). In the same post the company said its systems had “autonomously blocked hundreds of hyper-volumetric DDoS attacks” over recent weeks,…
Hackers Breach Fintech Environment, Attempted $130M Theft via Brazil’s Pix Network
Hackers Breach Fintech Environment, Attempted $130M Theft via Brazil’s Pix Network What happened On 2 September 2025, security reporting indicated that attackers gained unauthorized access to the environment of Evertec’s Brazilian subsidiary, Sinqia S.A., and attempted to steal $130 million by exploiting connectivity to Brazil’s central bank real‑time payment system, Pix. “Hackers tried to steal…
Lazarus Group Uses PondRAT, ThemeForestRAT and RemotePE in Social‑Engineering Strike on DeFi Organization
Lazarus Group Uses PondRAT, ThemeForestRAT and RemotePE in Social‑Engineering Strike on DeFi Organization Summary of the observed campaign Security researchers at NCC Group’s Fox‑IT observed a social‑engineering campaign in 2024 that has been attributed to the North Korea‑linked actor known as the Lazarus Group. The campaign distributed three distinct pieces of cross‑platform malware — named…
Cloudflare Says It Mitigated Record 11.5 Tbps Volumetric DDoS Attack
Cloudflare Says It Mitigated Record 11.5 Tbps Volumetric DDoS Attack What Cloudflare reported Internet infrastructure company Cloudflare said it recently blocked the largest recorded volumetric distributed denial-of-service (DDoS) attack, which peaked at 11.5 terabits per second (Tbps). Cloudflare said it recently blocked the largest recorded volumetric distributed denial-of-service (DDoS) attack, which peaked at 11.5 terabits…
DLP: What is it? And its main uses
What is Data Loss Prevention (DLP)? The definition of Data Loss Prevention encompasses a set of practices and tools designed to prevent data leakage (also known as data exfiltration) due to intentional and unintentional misuse. These practices and tools include encryption, detection, preventive measures, educational pop-ups (for unintentional movements), and even machine learning to assess…
Silver Fox Abuses Microsoft-Signed WatchDog Driver amsdk.sys to Deploy ValleyRAT
Silver Fox Abuses Microsoft-Signed WatchDog Driver amsdk.sys to Deploy ValleyRAT Overview Security researchers attribute a Bring Your Own Vulnerable Driver (BYOVD) campaign to a threat actor known as Silver Fox that leverages a previously unknown vulnerable Windows kernel driver to neutralize endpoint defenses and deploy ValleyRAT. The vulnerable component is a 64-bit, validly signed kernel…
Zscaler Salesforce Breach Exposes Customer Support Data After Salesloft/Drift Vendor Compromise
Zscaler Salesforce Breach Exposes Customer Support Data After Salesloft/Drift Vendor Compromise What happened Cybersecurity firm Zscaler has disclosed a data breach after threat actors gained access to its Salesforce instance and extracted customer information, including the contents of support cases. According to Zscaler’s notification and reporting by BleepingComputer, the intrusion followed compromises at third‑party vendors…
Zscaler Customer Data Exposed After Attackers Accessed Salesforce Instance
Zscaler Customer Data Exposed After Attackers Accessed Salesforce Instance Summary of the incident Cybersecurity vendor Zscaler has disclosed a data breach in which threat actors gained access to its Salesforce instance and exfiltrated customer information, including the contents of support cases. Zscaler warned customers about the incident and said the breach followed the compromise of…
Amazon disrupts Russian APT29 campaign targeting Microsoft 365 accounts
Amazon disrupts Russian APT29 campaign targeting Microsoft 365 accounts Summary of the disruption Amazon has been reported to have disrupted an operation attributed to the Russian state-sponsored threat group known as Midnight Blizzard (also tracked as APT29) that sought access to Microsoft 365 accounts and tenant data. Researchers who investigated the activity described the disruption…
ScarCruft (APT37) Deploys RokRAT in “Operation HanKook Phantom” Targeting South Korean Academics
ScarCruft (APT37) Deploys RokRAT in “Operation HanKook Phantom” Targeting South Korean Academics Summary of the discovery Cybersecurity researchers at Seqrite Labs have identified a new phishing campaign attributed to ScarCruft, an actor widely reported as North Korea–linked and also tracked as APT37. Seqrite has codenamed the activity Operation HanKook Phantom. According to the report, the…
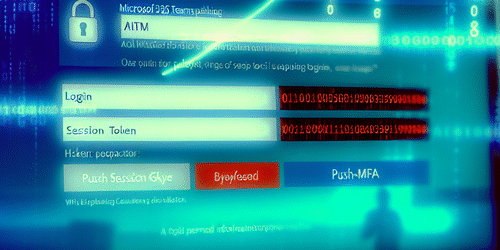
AiTM Phishing: How Attackers Use Session-Token Theft To Bypass MFA In Microsoft 365 — Detection And Prevention
Explore how AiTM phishing and session-token theft allow attackers to bypass Microsoft 365 MFA, why standard OTP methods fail, and which telemetry signals indicate compromise. This technical guide gives security teams practical detection queries, containment steps, and prevention controls—deployable playbooks to neutralize active AiTM campaigns and harden identity posture.
WhatsApp Issues Emergency Patch for CVE-2025-55177 Affecting iOS and macOS Linked‑Device Sync
WhatsApp Issues Emergency Patch for CVE-2025-55177 Affecting iOS and macOS Linked‑Device Sync What happened WhatsApp issued an emergency update for its iOS and macOS clients to remediate a high‑severity vulnerability the company said may have been used in targeted zero‑day attacks. According to WhatsApp, the bug — tracked as CVE‑2025‑55177 and assigned a CVSS score…
VS Code Marketplace Flaw Lets Attackers Reuse Deleted Extension Names, Researchers Warn
VS Code Marketplace Flaw Lets Attackers Reuse Deleted Extension Names, Researchers Warn Summary of the discovery Security researchers at ReversingLabs identified a loophole in the Visual Studio Code Marketplace that can be abused to republish extensions using the same names as previously removed packages. ReversingLabs reported the finding after it observed a malicious extension called…
VS Code Marketplace Flaw Lets Attackers Republish Names of Deleted Extensions
VS Code Marketplace Flaw Lets Attackers Republish Names of Deleted Extensions Summary of the finding Security researchers at ReversingLabs reported a weakness in the Visual Studio Code (VS Code) Marketplace that permitted actors to reuse the names of extensions that had previously been removed. The discovery followed the identification of a malicious extension named “ahbanC.shiba”…
MathWorks breach: ransomware gang exfiltrated data on more than 10,000 people
MathWorks breach: ransomware gang exfiltrated data on more than 10,000 people Overview of the incident MathWorks, the developer of MATLAB and Simulink, disclosed that a ransomware group breached its network in April and stole data relating to more than 10,000 people. The company reported the incident publicly after detecting the intrusion and the subsequent data…
Why Code-to-Cloud Mapping Is Becoming Essential for AppSec in 2025
Why Code-to-Cloud Mapping Is Becoming Essential for AppSec in 2025 The problem at a glance Picture this: developers push a change that looks harmless in a local environment but contains a subtle flaw that turns into a large-scale incident once deployed to cloud infrastructure. The vulnerability goes unnoticed until it is exploited, and the organization…
Storm-0501 Abuses Entra ID to Exfiltrate and Delete Azure Data in Hybrid Cloud Extortion Campaign
Storm-0501 Abuses Entra ID to Exfiltrate and Delete Azure Data in Hybrid Cloud Extortion Campaign Summary of the incident Recent reporting identifies a financially motivated threat actor tracked as Storm-0501 refining tactics to target hybrid cloud environments. The actor has been observed abusing Microsoft Entra ID (formerly Azure Active Directory) to gain access to Azure…
Cyberattack on Miljödata Disrupts Services Across More Than 200 Swedish Municipalities
Cyberattack on Miljödata Disrupts Services Across More Than 200 Swedish Municipalities What happened An attack targeting Miljödata, an IT-systems supplier used by roughly 80% of Sweden’s municipalities, has caused accessibility problems in more than 200 municipal regions, according to reporting by BleepingComputer. The supplier’s systems support a wide range of municipal IT services; the incident…
Over 28,200 Citrix Instances Exposed to Actively Exploited RCE (CVE-2025-7775)
Over 28,200 Citrix Instances Exposed to Actively Exploited RCE (CVE-2025-7775) Summary: What we know More than 28,200 Citrix instances are vulnerable to a critical remote code execution vulnerability tracked as CVE-2025-7775, and evidence indicates the flaw is already being exploited in the wild. The scale and active exploitation elevate this from a routine patch cycle…
DNS Tunneling Detection With Microsoft Sentinel: Spot Unusual NXDOMAIN, Long FQDNs, Base64 Patterns, Beaconing And Convert Sigma To KQL For Network Security Monitoring
Learn practical techniques to detect DNS tunneling and data exfiltration using Microsoft Sentinel. This guide shows how to spot unusual NXDOMAIN responses, long FQDNs, base64-like patterns and beaconing behavior, and includes Sigma-to-KQL guidance for fast deployment in network security monitoring. Take action now to harden your DNS telemetry and hunting playbooks.
Cibersecurity In 2025: Top Threats, Real Risks And Business Impact
Explore the evolving Cibersecurity landscape of 2025 to understand which threats—ransomware, supply-chain compromises, AI-assisted attacks and insecure IoT—pose the greatest business risks. This authoritative guide provides clear priorities, quick mitigation steps and a practical decision framework to protect operations, data and reputation. Read more to act now.
Why Zero Trust Network Access (ZTNA) Replaces VPNs: Architecture, Security, and Operational Gains
This technical playbook explains why Zero Trust Network Access (ZTNA) is the practical successor to legacy VPNs. Learn the architecture, core controls, SASE integration, and a phased migration plan to reduce attack surface, simplify operations, and improve security posture. Read on for actionable guidance to plan a safe, measurable ZTNA transition.
SIM-based authentication will put an end to phishing
Let’s face it: we all use email, and we all use passwords. Passwords create an inherent vulnerability in the system. The success rate of phishing attacks is skyrocketing, and opportunities for attack have multiplied enormously as life has moved online. All it takes is one compromised password for all other users to fall victim to…
Remote Desktop Protocol (RDP)
Remote Desktop Protocol (RDP) is a protocol, or technical standard, for using a desktop computer remotely. Remote desktop software can use several different protocols, including RDP, Independent Computing Architecture (ICA), and Virtual Network Computing (VNC), but RDP is the most widely used protocol. RDP was initially released by Microsoft and is available for most Windows…
How to protect the Linux Kernel
With the support of the open-source community and a strict privilege system built into its architecture, Linux has security built into its design. That said, gone are the days when Linux system administrators could get away with poor security practices. Cybercriminals have come to view Linux as a viable attack target due to its growing…
Kerberos: Implementation, Analysis, and Exploitation
What is Kerberos? Kerberos is a secure network authentication protocol based on tickets, designed to allow users and services to mutually authenticate over an untrusted network. Its main goal is to ensure that a user’s identity can be verified without transmitting passwords over the network, thereby reducing the risk of interception. Originally developed at MIT…
Attack methods: Content Spoofing
Content spoofing (also known as content injection) is one of the most common web security vulnerabilities. It allows the end user of the vulnerable web application to falsify or modify the actual content of the web page. Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not promote…
Attack methods: CSV injection
Online attacks are more frequent than ever, and this trend is likely to continue growing. In this article, we analyze CSV injection attacks and how to defend against them. Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not promote their use for profit or improper purposes. We…
How to dump the SMBShare
A script to remotely dump files and folders from a Windows SMB share Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not promote their use for profit or improper purposes. We are not responsible for any damage or impairment that may be caused to the systems used.…
Attack methods: Cross-origin resource sharing (CORS)
In this section, we will explain what Cross-Origin Resource Sharing (CORS) is, describe some common examples of attacks based on Cross-Origin Resource Sharing, and discuss how to protect against these attacks. Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not promote their use for profit or improper…
Kerberos Golden and Silver Ticket Attack
Today I bring you a very simple tutorial that many people have been asking me for. It’s about attacking Kerberos tickets, both golden and silver. First, to understand what Kerberos is, visit my post that talks about Kerberos Requirements: Responsibility: In this tutorial, we will use hacking techniques for educational purposes only. We do not…
Data Exfiltration and DLP in Corporate Environments + Lab
Data exfiltration—also known as Data Exfiltration—refers to the unauthorized transfer of sensitive information outside a secure corporate environment. This risk has become one of the top security concerns, as it can lead to theft of confidential information, reputational damage, and significant financial losses. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the…
LockBit Unleashed: How Ransomware is Redefining Cybersecurity Threats in 2024
This tutorial provides an in-depth exploration of the LockBit ransomware, one of the most sophisticated and dangerous ransomware strains in 2024. This blog is designed for cybersecurity professionals, IT administrators, and businesses aiming to understand the mechanics of ransomware attacks and how to defend against them. It combines technical insights, practical attack simulations, and mitigation…
Host Intrusion Detection System (HIDS)
Cybersecurity is a top priority in the digital age, where cyber threats to systems and networks are increasing every day. One of the key tools for protecting computer systems is the Host Intrusion Detection System (HIDS). This article details how HIDS works, its benefits and provides practical examples for a better understanding. What is a…
What is NAC and how does it work?
Security in corporate networks has become more complex with the increasing diversity of devices and users connecting to them. One of the most effective solutions for managing and securing network access is NAC (Network Access Control). This article explores in detail what NAC is, how it works, its components, and practical examples of its application…
Learning to exploit the Linux Kernel – Part 1
In this series, I’m going to write about some basics in Linux kernel exploitation that I’ve learned over the past few weeks: from basic environment configuration to some popular Linux kernel mitigations, and their corresponding exploitation techniques. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We do…
Active Directory Pentesting with Responder
Many people are asking me about Active Directory attack prevention methods and a good way for a critical vulnerability scan, which then leads me to get the domain administrator in fifteen minutes by simply exploiting misconfigurations in AD. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We…
Antivirus, what is it, why do I have to have it?
Nowadays we all know what an antivirus is, we know what we must have to stop a virus from entering our computer and making it unusable. The basic theory is fine, but to really know in depth what an antivirus does? I will explain in depth what it is and the reason for having it.…
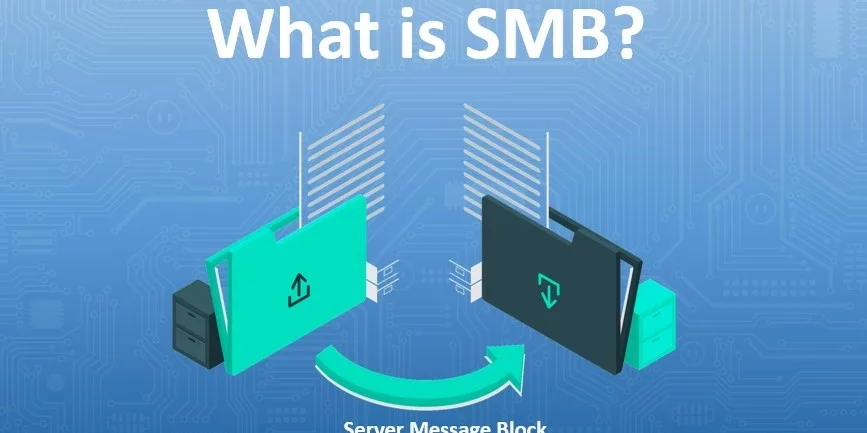
SMB What is it and how does it work?
Short for Server Message Block, SMB is an application layer protocol that enables file, printer and device sharing and inter-process communication (IPC) between applications on a network through a client-server architecture. In other words, computers (SMB clients) on a network can connect to SMB servers to access shared files and directories or perform tasks such…
Attack methods: Command Injection
Command injection is a cyberattack that involves the execution of arbitrary commands on a host operating system (OS). Typically, the threat actor injects the commands by exploiting an application vulnerability, such as insufficient input validation. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We do not promote…
CASB, what is it? and main uses
What is a CASB? According to Gartner, a cloud access security broker (CASB) is a security policy enforcement point, either on-premises or in the cloud, located between cloud service consumers and cloud service providers, whose purpose is to combine and enforce corporate security policies when accessing cloud resources. The CASB is like a policeman enforcing the laws…
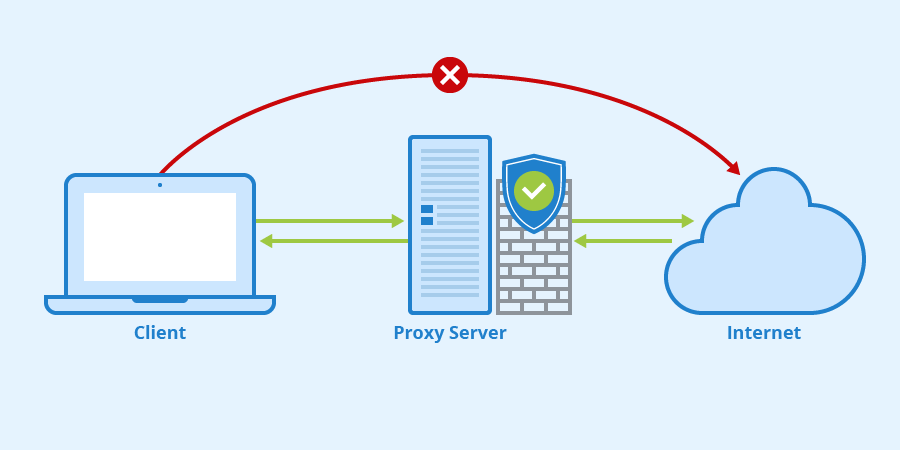
What is a proxy and what is it for?
A proxy is a well-known technology in the market, although sometimes it is not well understood how it works. Therefore, in this opportunity we will explain what a proxy is and how it is useful. But before we start talking about the logical structure of proxy servers, I consider it important to clarify how it…
Attack methods: Code Injection
Code injection is the general term for attack types that consist of injecting code that is then interpreted/executed by the application. This type of attack takes advantage of mismanagement of untrusted data. Requirements: Responsibility: In this tutorial we will use hacking techniques, with the only purpose of learning. We do not promote its use for…
How to configure PROXYCHAINS in KaliLinux via Terminal
Proxychains is an open source software for Linux systems and comes pre-installed with Kali Linux, the tool redirects TCP connections through proxies such as TOR, SOCKS4, SOCKS5, and HTTP (S) and allows us to chain proxy servers. With proxychains, we can hide the IP address of the source traffic and evade IDS and firewalls. Requirements:…
Access Windows 10 without knowing the password
Surely more than one has happened to you that you have forgotten the password of your windows or a Windows 10 that was in domain is not able to access the AD. In this tutorial I will show you how to enter the machine without knowing the password, either physical or virtual machine (in this…
DNSSEC What is it?
One of the cornerstones of the Internet is the Domain Name System, also known by its acronym DNS. The purpose of this protocol is to translate the domain names used by users into IP addresses that can be interpreted by machines. This protocol dates back to the 1980s, a time when functionality prevailed over security, and DNS was…
What is Kerberos, how does it work and what is it used for?
Cybercrime is an unfortunate fact of life today, regardless of whether we are talking about individual consumers or the business world in general. No company or organization is safe, and the problem is not going to get better any time soon. Experts predict that the damage caused by cybercrime will cost the world $6.1 trillion…
Attack methods: Clickjacking
Clickjacking is an attack that tricks the user into clicking on a web page element that is invisible or disguised as another element. This can cause users to unintentionally download malware, visit malicious web pages, provide credentials or sensitive information, transfer money or purchase products online. Requirements: Responsibility: In this tutorial we will use hacking…
Install Linux Subsystem for Windows
The Linux Subsystem for Windows continues to advance in capability and also in ease of use. Earlier this year, Microsoft promised an update to make it and GNU/Linux distributions easier to install, and has just implemented it in the latest Windows 10 Insider Preview Build 20246. Four years ago Microsoft announced a bombshell at its…
How to stop a DDoS attack?
Imagine your website is a store, Distributed Denial of Service (DDoS) is like a mob in front of your store that won’t let your customers in. It’s a nasty situation to have tens of thousands of fake shoppers eating up your valuable resources, all at once. Know how to stop DDoS attacks. DDoS has become…
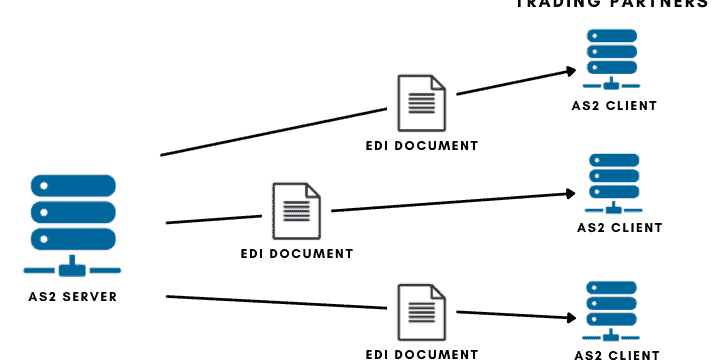
AS2 protocol and differences with SFTP
How are sensitive sectors such as commercial airlines, healthcare or transport communicated and shared data? How do you transfer structured B2B data safely and reliably through risk networks like the Internet? The answer is the AS2 protocol. What is AS2? Applicability Statement 2 ( AS2 ) is a type of file transfer mechanism based on…
Methods of attack: Brute Force Attack
What is the brute force attack method? A brute force attack uses the trial and error method to guess access information, encryption keys, or find a hidden web page. Hackers work through all possible combinations in hopes of guessing correctly. These attacks are carried out by « brute force », which means that they use…
SQL Injection with sqlmap
What is SQLmap? SQLmap is a tool developed in python to automate attacks of the SQL Injection type. Its objective is to detect and take advantage of existing vulnerabilities in web applications. Once one or more possible injections have been detected, the user has the possibility to choose from a variety of options, such as listing…
Permanent backdoor on the remote PC
¿What is the persistent back door? As we know that persistence is also known as permanent. Persistent back doors help us have permanent access to the system. There are many types of persistent rear doors but they work similarly. Usually, the attacker create a backdoor service with the help of metasolpit frame and load in…
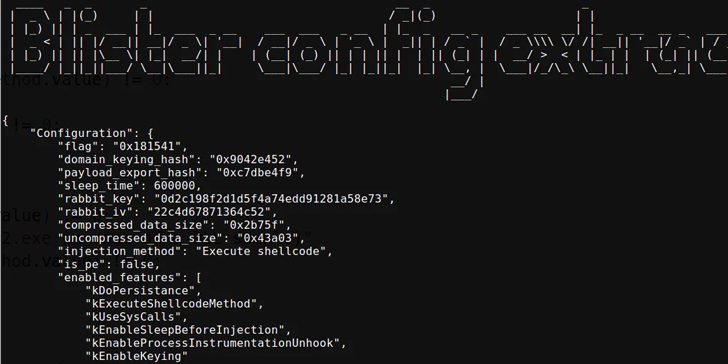
Revisting BLISTER
Preamble In a fast-paced and ever-changing world of cybercrime threats, the tenacity and adaptability of malicious actors is a significant concern. BLISTER, a malware loader initially discovered by Elastic Security Labs in 2021 and associated with financially-motivated intrusions, is a testament to this trend as it continues to develop additional capabilities. Two years after its initial discovery,…
Decrypt user passwords on a Linux system
In this article, we’ll see how to get password hashes from a Linux system and crack the hashes probably using the most widely used password decryption tool, John the Ripper. Requirements: Reposability: In this tutorial we will use hacking techniques, for the sole purpose of learning. We do not promote its use for profit or incorrect…
What is an EDR? Why is it different from an antivirus?
In a world where cyber threats change and evolve at practically the same speed as technology itself, security solutions are needed that not only react to the threat, but are able to anticipate it. Within those proactive solutions we have the EDR system; In this article we explain what it is, how it works and how…
SSH What is it? ¿How does it work?
SSH or Secure Shell, is a remote administration protocol that allows users to control and modify their remote servers over the Internet through an authentication mechanism. Provides a mechanism to authenticate a remote user, transfer entries from the client to the host, and retransmit the output back to the client. The service was created as…
Email Phishing Using Kali Linux
No matter how often you connect and how or why you mainly use the Internet, you have probably seen phishing attack attempts. They are now so common and problematic that cybersecurity professionals regularly provide information to help people detect and avoid phishing attacks. Requirements: Reposability: In this tutorial we will use hacking techniques, for the…
Attack methods: Cache Poisoning
Imagine that, as a high school senior prank, the high school students change all the room numbers in the high school facilities, so that new students who don’t know the high school floor plan yet will spend the next day lost and going to the wrong classes. Now imagine that mismatched room numbers get recorded in…
Top 10 Cybersecurity Trends for 2023: From Zero Trust to Cyber Insurance
As technology advances, cyberattacks are becoming more sophisticated. With the increasing use of technology in our daily lives, cybercrime is on the rise, as evidenced by the fact that cyberattacks caused 92% of all data breaches in the first quarter of 2022. Staying current with cybersecurity trends and laws is crucial to combat these threats, which can…